Best Blog for free hacks
January 11, 2010
Google Nexus One costs $174.15
June 28, 2009
Airtel Hack for free internet
First thing make sure your DSL modem is on. Start your browser. Type http://192.168.1.1 as the address with Username : admin Password : password
Note : These are case sensitive. Make sure all are typed in lowercase. Click on Advanced Setup -> NAT in the page that loads. If you do not see these options try entering http://192.168.1.1/main.html as the address. Some routers/modems deliberately try to prevent users from accessing these options. On the NAT virtual servers page click the add button. Now add the port number that you wish to open up. You can even open up a range of ports using the add button. You should see something similar to the screenshot below. Click it to view full image
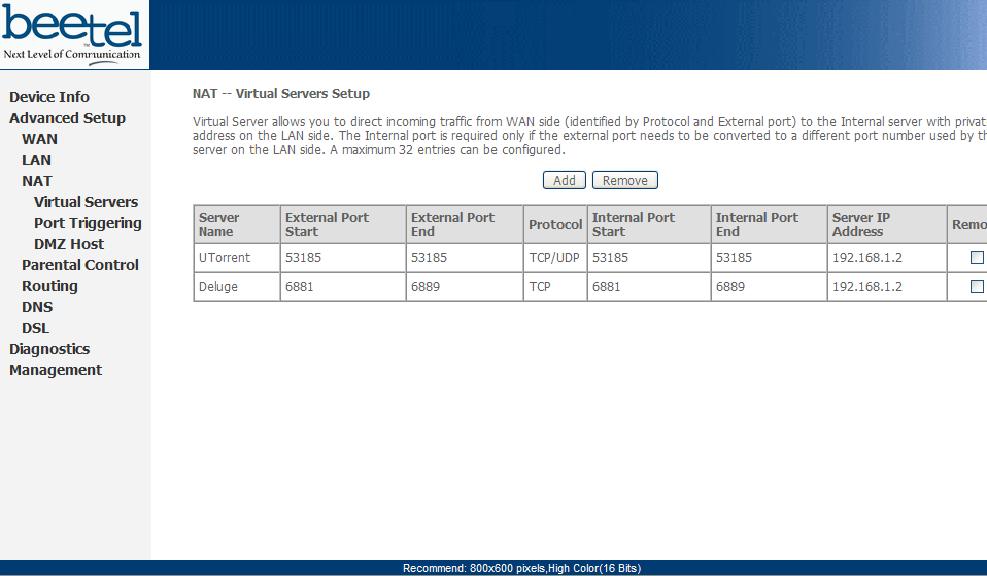
This technique can be used for any operating system / modem / service provider. It may vary slightly but the essential principle remains the same.
You need a PC or a Laptop and the required connectivity tools ,ie.,
Serial/USB cable OR Infrared Device OR Bluetooth dongle
1) Activate Airtel Live! ( It’s FREE to activate so no probs)
2) Create TWO Airtel gprs data accounts (TWO) and select the
FIRST as the active profile.
3) Connect your mobile to the PC (or Laptop) and install the driver for
your mobile’s modem.
4) Create a new dial-up connection using the NEW CONNECTION
WIZARD as follows
Connecting Device : Your mobile’s modem
ISP Name : Airtel (or anything you like)
Phone Number : *99***2# / Try 99***1
Username and Password : blank
5) Configure your browser and download manager to use the proxy
100.1.200.99 and port 8080.( My advice is to use Opera since you
can browse both wap and regular websites)
6) Connect to the dial-up account. You will be connected at 115.2
kbps (but remember, that is a bad joke).
7) Pick up your mobile and try to access any site. You will get “Access
Denied…”(except for Airtel Live!). IT DOES NOT MATTER.
Keep the mobile down.
8 ) On the PC ( or Laptop) open your browser, enter any address ,
press ENTER and…….WAIT
9) After a few seconds the page will start to load and you have the
WHOLE internet at your disposal. ***************************************************************************************************************
TWO
Under DATA COMMAPN : airtelfun.com
USERNAME : blank
PASSWORD : blank
PASS REQ : OFF
ALLOW CALLS : AUTOMATIC
IPADDRESS :
DNSADDRESS :
DATA COMP : OFF
HEADER COMP : OFF
Under INTERNET PROFILES
INTERNET MODE : HTTP or WAP (both worked for me)
USE PROXY : YES
IP ADDRESS : 100.1.200.99
PORT : 8080
USERNAME :
PASSWORD :
No Risk Here, Try it and Enjoy
Three
1st go to settings menu then to connectivity tab now choose the option Data comm. then "DATA ACCOUNTS" go to new account now the settings r as followsACCOUNT TYPE:GPRS
NEW ACCOUNT NAME:A1
APN:airtelfun.com
usr name: (blank)
password: (blank)
now save it
NOW!
go to Internet Setting in connectivity here choose intrnet profile--go to new profile setting are as below
NAME:A1
CONNECT USING:A1(which was created in data comm.)
save it
now u would be able to see it now selest it and take "more" option then select setting here in use proxy option it will be selected no if it is no then change it into yes
now go to proxy adress and give the adress as
100.1.200.99 and then the port number as 8080
Usr name:
password:
now save all the settings u made . come back 2 connectivity
choose streaming settings now in connect using option choose a1 that we created leave the use proxy option as no itself
THESE R THE SETTINGS
now access airtellive! from ur activated SE phone goto VIDEO GALLERY OR VIDEO UNLIMITED(varies according to states) choose live streaming then choose CNBC OR AAJTAK WHILE CONNECTING TO MEDIA SERVER cancel AFTER 9 or 10 sec then type any web adress if it shows access denied then once again select CNBC and wait for a few more sec than before if its fully connected also no prob its free then cancel it or if ur connected then stop it and the internet is ready to take of .GOOD LUCK SE AIRTEL USERS
February 25, 2009
Free iTunes Store Account
Free iTunes Store Account - No matter where you live :
Many of you might think that iTunes Store Account is a premium account and it is not at all free.
Because you might have seen the page on the account setup asking for your credit card information or any other payment method or so.
Well, there is a way you can get an iTunes Store Account for free.
This way of getting the iTunes Store Account for free is perfectly legal, it is also approved by Apple and there is no sort of gambling or so.
This account of iTunes store (free) can be used on any of the Apple sites and services.
And mostly this can be used with Genius in iTunes.
You just need to follow the following steps:
1. Select the iTunes store in which you did like to have an account. Use the store selector towards the bottom of the iTunes store homepage.
2. Choose the App store, then select one of the Free Apps.
3. When the app page loads, hit the 'Get App' button.
4. The login prompt will appear so be sure to click on 'Create New Account'
5. Click continue, then tick the 'I Accept' box, and click Continue again.
6. Fill out your details on the next page (you'll need a real, valid email address), and click continue
7. After that, fill out your details.
8. You will now see a message telling you to click on the confirmation link sent to the email you specified earlier. Then check your email inbox ( or spam folder ), open the email and click the confirmation link.
9. iTunes will popup, and here you will sign in with your new iTunes account details'
10. You should now have successfully logged into your free Account.
So go get your new iTunes store accounts for free and that too perfectly legal.
Done. :)
December 20, 2008
Self destructing Email
Until now, everyone else has had control of the email that you have sent. Big String gives you back control of your email, acting like an automatic shredder for your email. You can self-destruct or change an email that's already been sent or read. Don't leave your messages sitting in peoples' inboxes forever. Get a free Big String email account to protect your privacy.
BigString takes the risk out of email
Now, with BigString, you can finally take the risk out of email and put an end to "sender regret." It is the world's first & only email service that thoroughly protects your safety and privacy.
BigString's exclusive, patent-pending technology enables you to prevent your personal or business information from lingering indefinitely in someone else's inbox. It also restricts private pictures or messages from being indiscriminately spread throughout cyberspace! Now your sensitive photos can't be posted to unseemly web sites or printed for circulation amongst total strangers.
BigString lets you have second thoughts
BigString shifts the control from the recipient to YOU the sender. BigString grants the luxury of second thoughts, the power to limit message viewings, and the choice to delay email transmission.
You can reword a message fired off in anger or haste or completely delete it! You can recall a botched résumé for revision or erase a tasteless joke. You can make a work of art or photograph print-proof. You can prevent a love letter from being forwarded. You can set an expiration date on an emailed price quote or business offer or you can simply pull back an email to eliminate typos.
BigString takes the danger out of clicking
BigString guarantees that clicking "send" will never again be an irreversible disaster. Now YOU decide the fate of your emails. You decide where they end up, who sees them and for how long. BigString emails can be destroyed, recalled or changed even after they've been opened! The freedom is yours, the options are yours, and you're the boss with BigString.
BigString is easy to use
BigString is as easy to use as any other email and there's nothing to download! Don't be resigned to the mercy of your recipient. You don't want your every action to be carved in stone because sometimes you just NEED to take it back!
Here are just a few of the many applications of BigString
Erasable, Recallable, Non-Printable Email.
Executives: Protect your business and safeguard your email. Now you never have to worry about sending the wrong attachment or completely forgetting it. Misspelled words, incorrect dates, or other typos can all be fixed even after your message has been sent. You can even "pull an email back" to delete expired price quotes, old business offers or dated legal material. BigString is your email insurance.
On-Line Daters: You don't want your personal information like pictures, phone numbers or intimate notes, circulated around the Internet! BigString prevents your pictures and messages from being printed or forwarded. You can set an expiration date for an email or self-destruct it at will. You can choose the number of times you'll allow a picture to be viewed before it disappears. BigString protects your privacy!
Artists and Photographers: Now with BigString you can confidently email proofs and samples without the slightest fear that they will be printed or saved for later use without your authorization. Use BigString to make your image non-savable and non-printable! Limit the number of times a client can view a piece before you have it self-destruct. You can even recall a sent email to delete an old price quote or alter a new one. You can also prevent it from being forwarded to other customers. BigString protects your rights of ownership!
Copywriters: Spelling or punctuation errors that can cost time, money, or embarrassment are now a thing of the past. With BigString, clicking "send" is no longer an action "carved in stone." Accidentally arranging paragraphs in the wrong order will no longer mean a lost account. With the technology of BigString you can recall that mistake-ridden copy and correct the errors even after your email has left the outbox. You can self-destruct what you sent all together and replace it with a fully revised version. Only you will know this switch has occurred! With BigString you can confidently send non-printable, non-savable sample copy. You no longer have to worry that it will be used without your knowledge. You're the boss with BigString.
All the features of Regular Email plus:
Recallable/Erasable Email
Non-Forwardable Email
Non-Printable/Savable Email
Advanced Email Tracking
Masquerading
All the storage you need
Video Email
Large Attachment Capacity
Automatic Message Highlighting
Advanced Spam and Virus Filtering
Advanced Message Sorting
Fun Email Effects
December 9, 2008
Anonymizers and Remailers !! What n How
How do Anonymizers work?
You essentially surf the Web through the anonymizer site, going to that site first and then routing all your pages from there. When you send a page request through the anonymizer, it acts like a super-proxy server, stripping off the header of each data packet, thus making your request anonymous. The requested page is then fed through the anonymizer back to your Web browser**.
In order to avoid being tracked, one can use an anonymous proxy to surf the web. An anonymous proxy makes sure your IP address does not get stored on the web server logs. Web servers log every ?GET? request made, together with date, hour, and IP. But if you are accessing the Internet through a proxy server, then the IP of the proxy is logged and not yours.
In case you do not go through an anonymous proxy, then you are actually risking vital information that belongs to you. For example, a hacker can easily find out your IP Address, your web browser, your Operating System and even the previous URL that you have visited. You can also be easily located geographically (provided one has the necessary software tools) because people can find out a whole lot of things that give your location. Like your hostname, your continent, your country, your city and even your Internet Service Provider.
Consider the scenario where a hacker gets access to your computer, he can find out your name, email address, telephone number, various user ID's and passwords, details about software you use and your preferences, locations of files and folders, the search strings that you used and literally hundreds of other personal things. All this information is stored in files like SYSTEM.ini, USER.dat, SYSTEM.dat etc. One very important file is the nsform??.TMP which stores all the data inside every Netscape form you've ever submitted, with and without SSL, when the submission failed or was cancelled.
What are Re-mailers?
Anonymous Re-mailers are services used to send e-mail messages, so that the recipient of the e-mail cannot determine the identity of the sender. Re-mailers strip off header information leading to the identity of the sender and often route a message through a chain of re-mailers before reaching the recipient. Many re-mailers also include some sort of message based encryption. Re-mailers are commonly used to protect the anonymity if the sender from the recipient, to prevent eavesdropping by a third party, or to post anonymously to newsgroups*.
How do Re-mailers Work?
An anonymous re-mailer is simply a computer connected to the Internet that forwards electronic mail or files to other addresses on the network. It also strips off the "header" part of the messages, which shows where they came from and who sent them. All the receiver can tell about a message's origin is that it passed through the re-mailer. Some re-mailers also allocate each sender an "anonymous ID", rather like a PO Box number, which it stores with the sender's address so that any replies reach them.***
All re-mailers are fairly effective at what they do and some even take an extra step and add encryption to all outgoing messages. In order to view header information sent via email messages in Outlook Express, select a message in your inbox, then select File | Properties | Details.
To view header information in m*c*s*t Outlook, right-click a message in your inbox and select Options; the header information is displayed in the Internet Headers area of the Message Options dialog box.
Anonymous re-mailers were invented by security experts interested to know whether it was possible to send a message on the Internet which could not be traced back to its source. As soon as the first ones were built, though, people found a more pragmatic use for them: to send messages to bulletin boards about subjects so sensitive that they did not want their names known.